ESET has collaborated with Microsoft, BitSight, Lumen, Cloudflare, CleanDNS, and GMO Registry in a global disruption operation against Lumma Stealer, an infamous malware-as-a-service (MaaS) infostealer. The operation targeted Lumma Stealer infrastructure with all known C&C servers in the past year, rendering the exfiltration network, or a large part of it, nonoperational.
Key points of this blogpost:
- ESET took part in a coordinated global operation to disrupt Lumma Stealer.
- ESET provided technical analysis and statistical information, and extracted essential data from tens of thousands of malware samples.
- We provide an overview of the Lumma Stealer MaaS ecosystem.
- We also provide technical analysis and an overview of the evolution of Lumma Stealer’s key static and dynamic properties, which were critical to the disruption effort.
Disruption contribution
ESET automated systems processed tens of thousands of Lumma Stealer samples, dissecting them to extract key elements, such as C&C servers and affiliate identifiers. This allowed us to continuously monitor Lumma Stealer’s activity, track development updates, cluster affiliates, and more.
Infostealer malware families, like Lumma Stealer, are typically just a foreshadowing of a future, much more devastating attack. Harvested credentials are a valued commodity in the cybercrime underground, sold by initial access brokers to various other cybercriminals, including ransomware affiliates. Lumma Stealer has been one of the most prevalent infostealers over the past two years, and ESET telemetry (see Figure 1) confirms that it has left no part of the world untouched.
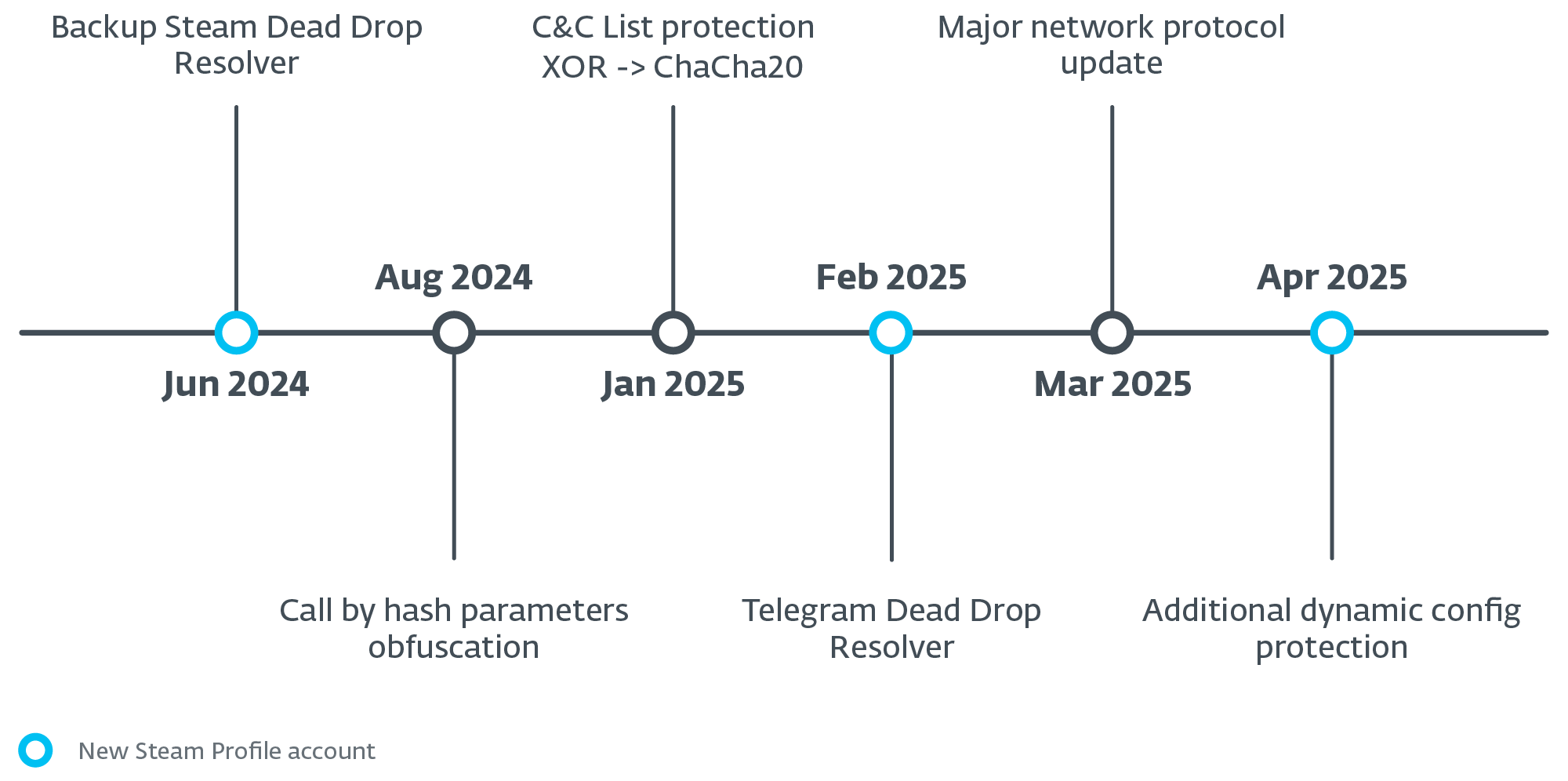
Lumma Stealer developers had been actively developing and maintaining their malware. We have regularly noticed code updates ranging from minor bug fixes to complete replacement of string encryption algorithms and changes to the network protocol. The operators also actively maintained the shared exfiltration network infrastructure. Between June 17th, 2024 and May 1st, 2025, we observed a total of 3,353 unique C&C domains, averaging approximately 74 new domains emerging each week including occasional updates to Telegram-based dead-drop resolvers (see Figure 2). We discuss the details of the network infrastructure later in the blogpost.
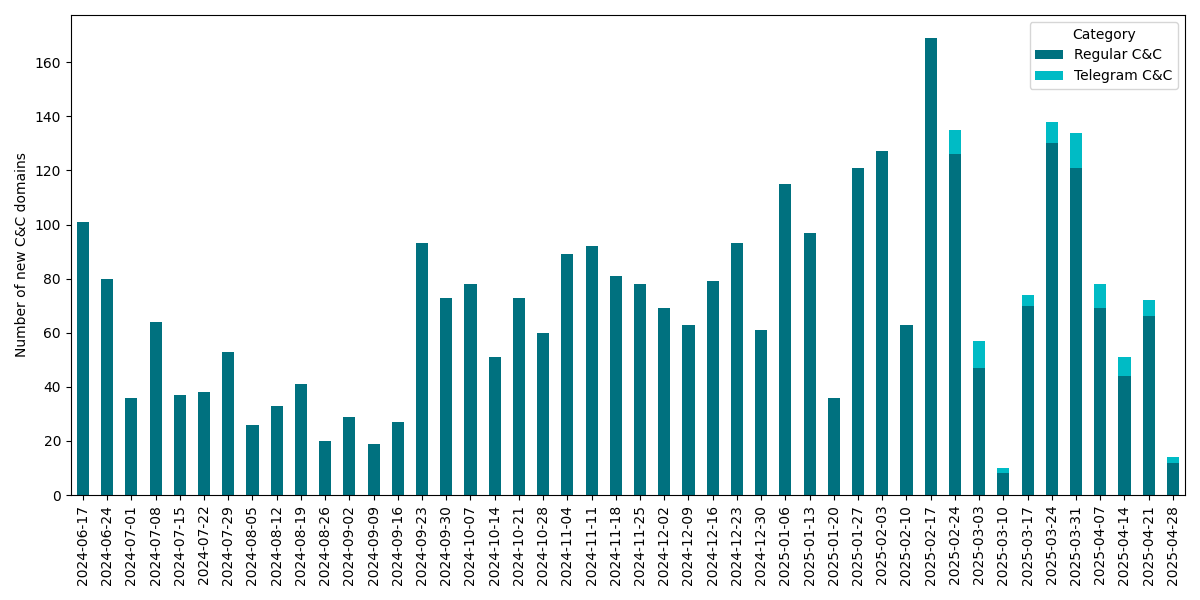
This ongoing evolution underscores the significant threat posed by Lumma Stealer and highlights the importance and complexity of the disruption effort.
Background
Over the past two years, Lumma Stealer (also known as LummaC or LummaC2) has emerged as one of the most active infostealers in the cybercrime ecosystem, becoming a favored tool among cybercriminals due to its active development of malware features and its infrastructure being sold as a service.
Malware as a service
Lumma Stealer adopts the concept of malware as a service (MaaS), where affiliates pay a monthly fee, based on their tier, to receive the latest malware builds and the network infrastructure necessary for data exfiltration. Affiliates have access to a management panel with a user-friendly interface where they can download exfiltrated data and harvested credentials.
The tiered subscription model ranges from USD 250 to USD 1,000 per month, each with increasingly sophisticated features. Lower tiers include basic filtering and log download options, while higher tiers offer custom data collection, evasion tools, and early access to new features. The most expensive plan emphasizes stealth and adaptability, offering unique build generation and reduced detection.
The operators of Lumma Stealer have also created a Telegram marketplace with a rating system for affiliates to sell stolen data without intermediaries. The marketplace has been well documented in Cybereason research. Moreover, they maintain public documentation of the management panel for affiliates and periodically share updates and fixes on hacking forums, as shown in Figure 3.
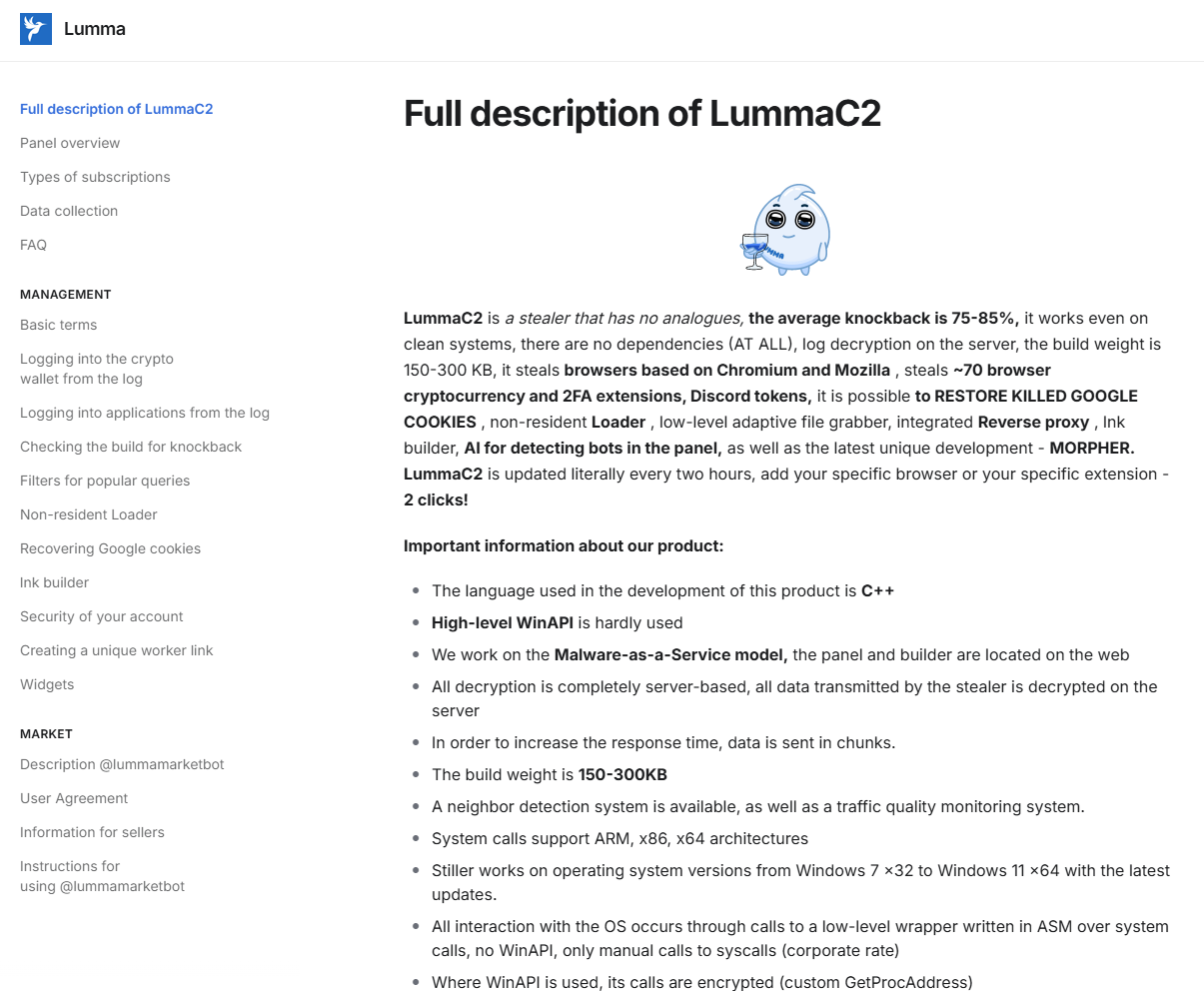
Open documentation not only helps affiliates with less experience to use the malware service, but also provides valuable insights for security researchers. Developers focus on malware builds, data pipelining, and infrastructure maintenance, while affiliates are responsible for distributing the malware. This information, combined with the service’s popularity, results in a wide variety of compromise vectors.
Common distribution methods include phishing, cracked software, and other malware downloaders including SmokeLoader, DarkGate, Amadey, Vidar, and others. Popular phishing schemes involve ClickFix or fake CAPTCHA web pages, fraudulent forums with cracked software, fake GitHub repositories, fraudulent links on Reddit forums, and many more.
Technical analysis
Numerous public analyses have already been written about Lumma Stealer and its compromise vectors. Our focus here, however, is on the aspects relevant to the disruption. In this section, we will briefly introduce the key static and dynamic properties that we have been actively extracting from Lumma Stealer.
Static properties of Lumma Stealer
Various information comes embedded in Lumma Stealer malware samples. This naturally presents an ideal target for automated extraction. Besides the obvious data of interest – C&C server domains – the samples also contain identifier strings that tie the sample to a specific affiliate and a campaign, and an optional identifier leading to a custom dynamic configuration. These identifiers are used in network communication with the C&C server during data exfiltration and requests for dynamic configuration. In the sections below, we look at these properties in depth.
C&C domains
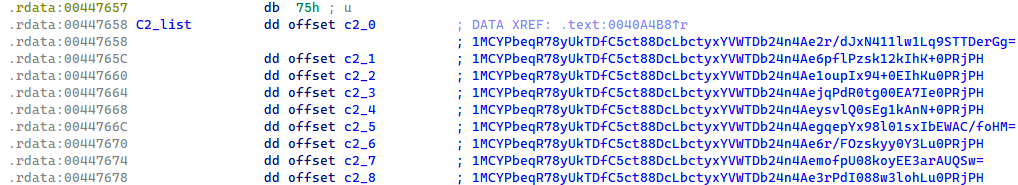
Each Lumma Stealer sample contains a list of nine encrypted C&C domains. While the encryption methods have evolved over time, the characteristic array structure has remained consistent up to the time of writing.
Based on Lumma Stealer’s internal sample versioning, which is heavily protected by stack string obfuscation, we know that up until January 2025, the C&C domains in the samples were protected by an XOR function and base64 encoding (see Figure 4). When the base64-encoded string was decoded, it revealed a structure where the first 32 bytes served as an XOR key, and the remaining bytes contained the encrypted C&C domain.
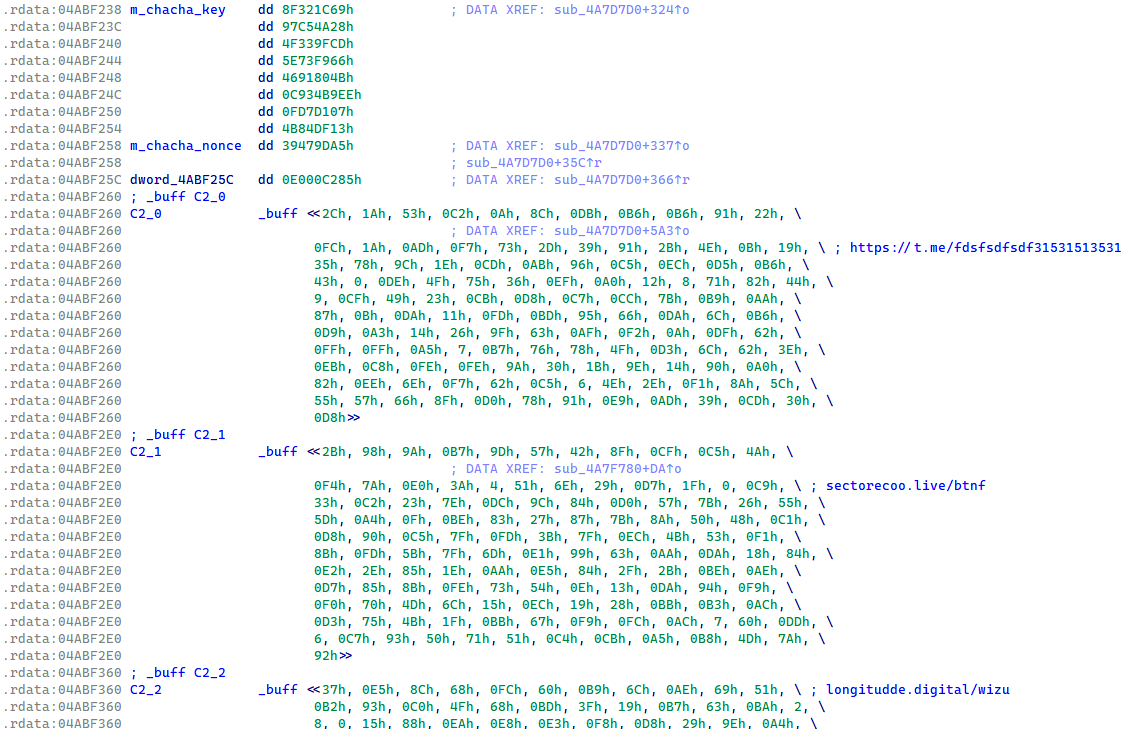
In January 2025, Lumma Stealer transitioned the protection of the C&C list to ChaCha20 encryption with a single hardcoded key and nonce (see Figure 5). This protection of the C&C list in the Lumma Stealer binaries has remained the same up until the time of publication.
Dead-drop resolvers
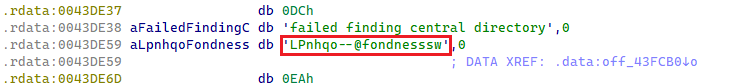
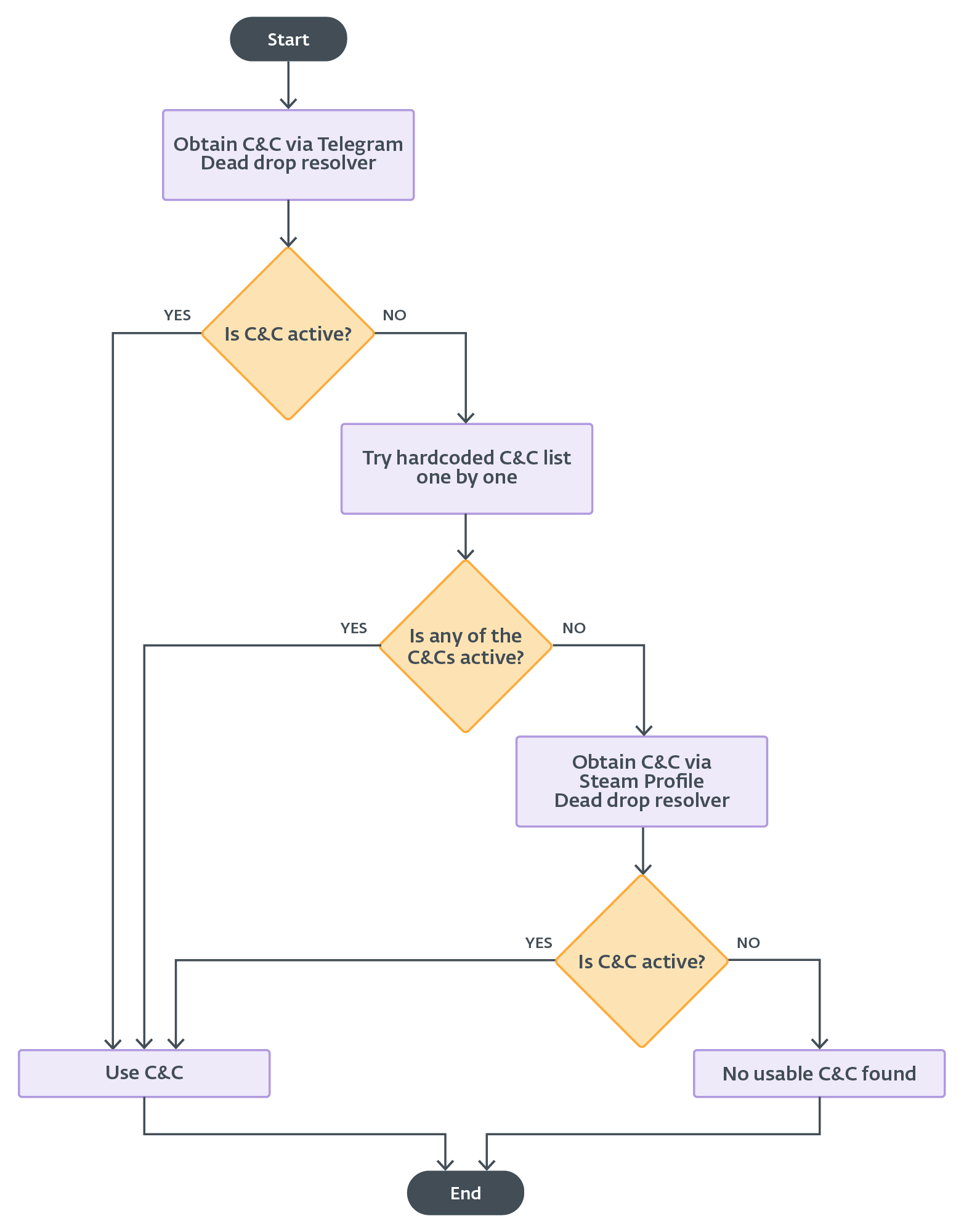
Since June 2024, each Lumma Stealer build came with a new feature for obtaining a backup C&C. If no C&C server from the static config responds to Lumma Stealer, then the backup C&C is extracted from a dummy Steam profile web page acting as a dead-drop resolver. The Steam profile URL is heavily protected in the binary, the same way as the version string. The encrypted backup C&C URL is set in the Steam profile name, as shown in Figure 6, and the protection is a simple Caesar cipher (ROT11).

In February 2025, Lumma Stealer received an update that included a feature for obtaining a new, primary C&C URL from a Telegram channel dead-drop resolver. The C&C URL is extracted from the Telegram channel’s title field, and it is protected by the same algorithm as in the case of the Steam profile dead-drop resolver. The main difference in the usage of the Telegram and Steam profile dead-drop resolvers is that the Telegram option is tested first, while the Steam profile is used as a last resort if successful communication has not been established with previously obtained C&C servers (Figure 16).
Moreover, we believe that the Telegram dead-drop resolver is available for higher tier subscriptions. This is because many samples do not have the Telegram URL set, and therefore the malware skips this method.
Lumma Stealer identifier
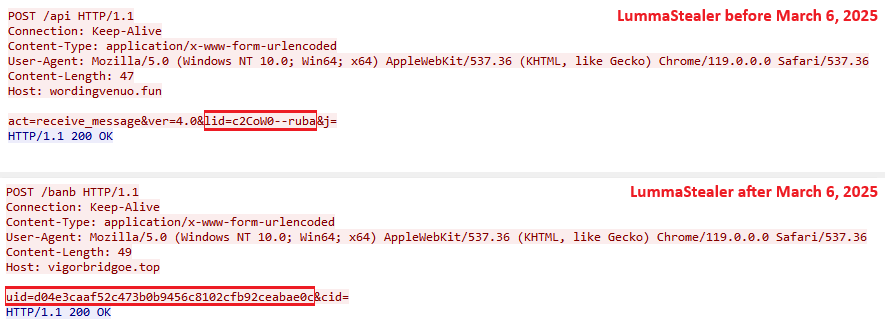
Each Lumma Stealer sample contains a unique hardcoded affiliate identifier known as LID. It is embedded in plaintext form and utilized for communication with C&C servers. Up until March 2025, the LID parameter string followed a structured format, delimited by two dashes (Figure 7). A detailed analysis of the LID affiliate string is provided in an upcoming section.
Although the most prevalent LID observed during our tracking begins with the string uz4s1o; the second most common LID, which starts with LPnhqo, provides a better example for visualizing typical LID variability. In the word cloud in Figure 8, we present the top 200 LIDs collected during our tracking, starting with LPnhqo.

However, in early March 2025, Lumma Stealer transitioned to using hexadecimal identifiers, referred to internally as UID (see Figure 9).
Optional configuration identifier
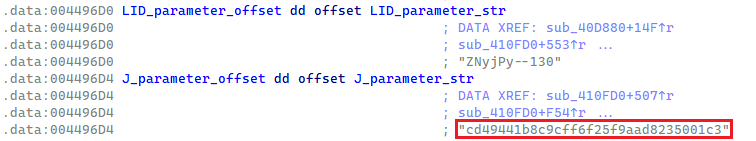
In addition to the LID parameter, Lumma Stealer samples may also contain an optional parameter referred to internally as J. When present, this parameter is in cleartext and formatted as a 32-byte ASCII hex string (see Figure 10). The J parameter is utilized in the C&C request for dynamic configuration with additional definitions for exfiltration. We talk about dynamic configuration in more detail in a following section.
If the J parameter is missing in the Lumma Stealer sample, an empty string is used in the C&C request and a default configuration is retrieved. Unlike LID, the J parameter is rarely present in Lumma Stealer samples. However, it plays a crucial role when present, as it enables retrieving a dynamic configuration that significantly increases the stealer’s capabilities, making it a more versatile exfiltration tool for threat actors.
In March 2025, when the LID parameter was renamed to UID and its format changed, the J parameter was renamed to CID but with no change to its format or function.
Analysis of static properties
From our long-term tracking and statistical analysis of LID parameters, we believe that the first segment of the LID identifies the affiliate, while the second segment differentiates between campaigns. Based on this assumption you can see the top 200 affiliate identifiers in Figure 11.
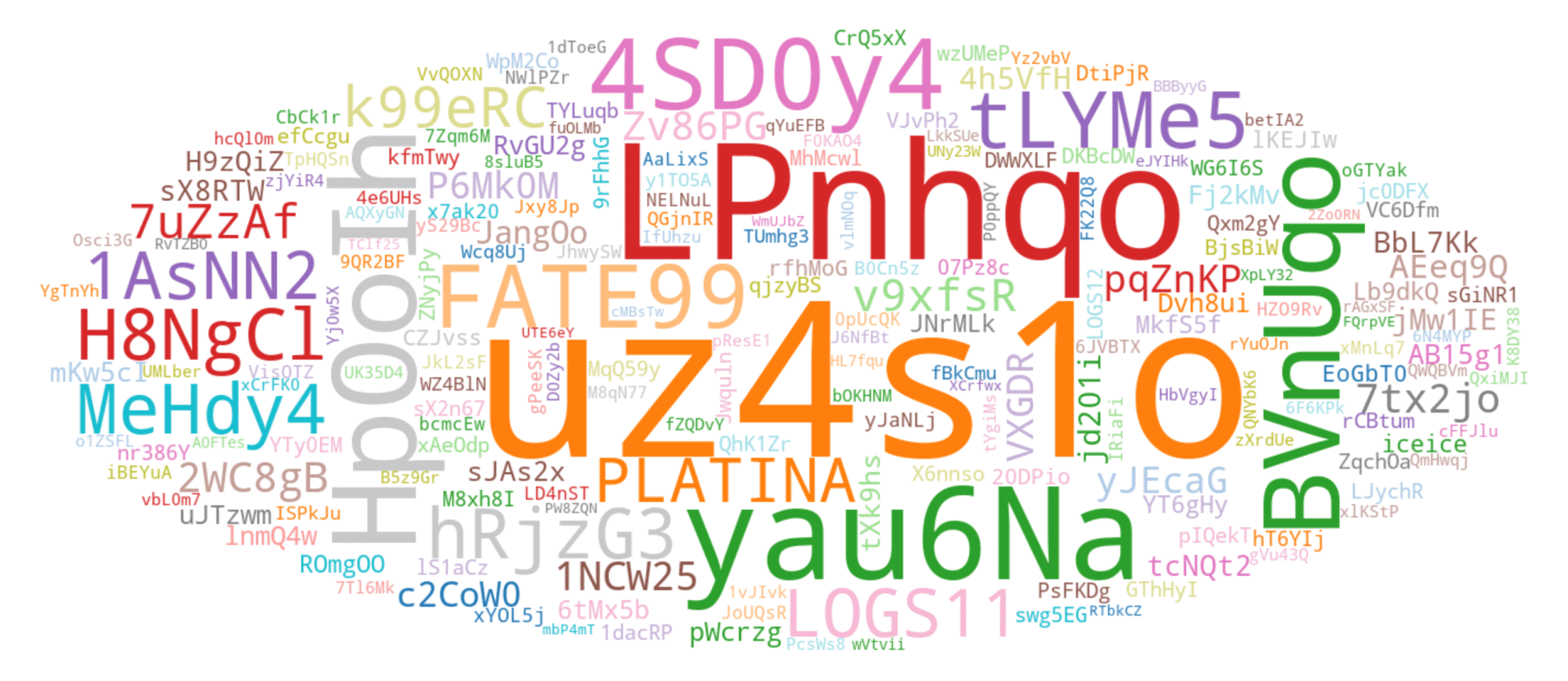
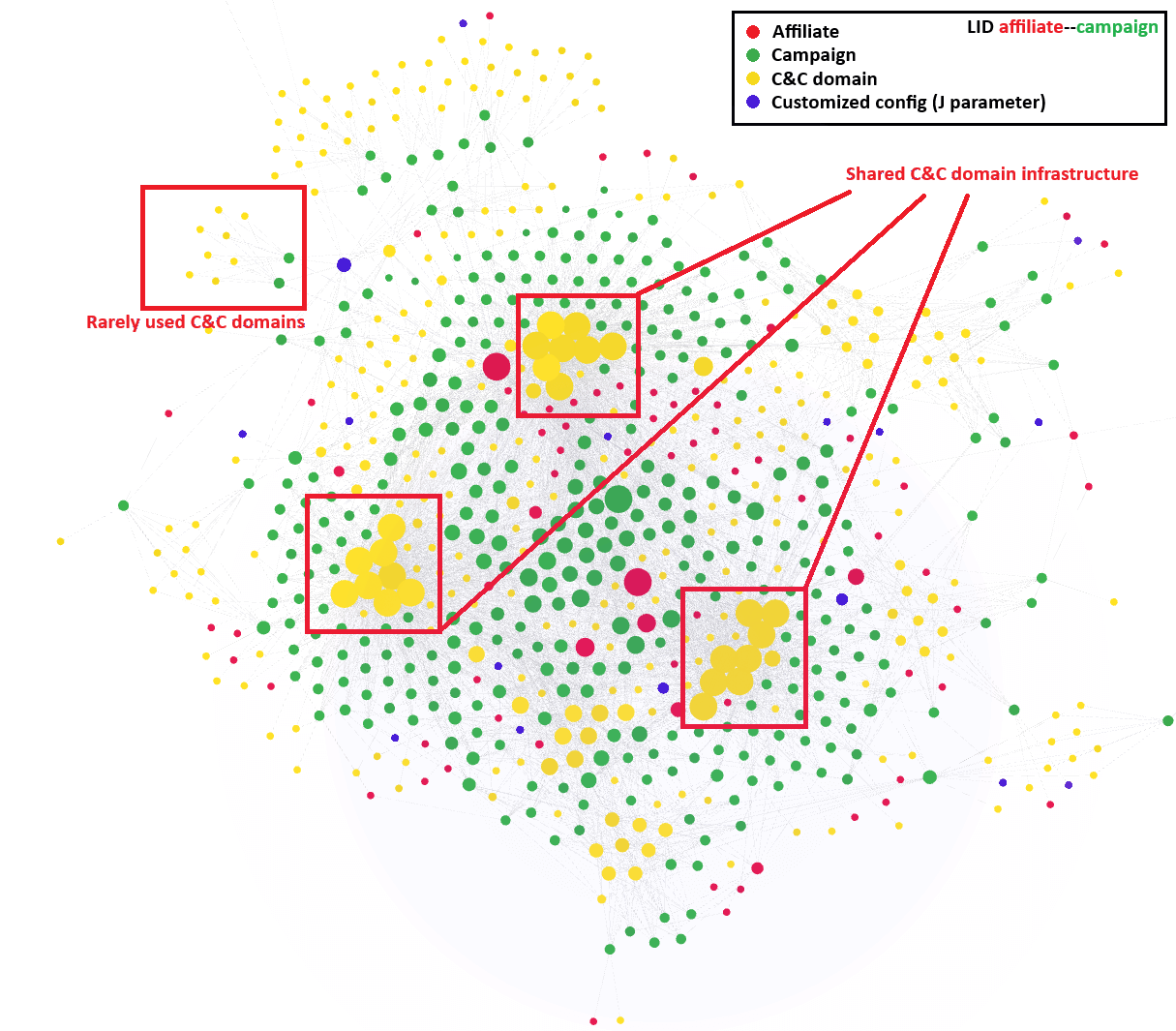
Moreover, we have been able to create a visualization of the affiliates’ activities over the past year (see Figure 12). This visualization highlights a week in January 2025. These types of visualizations have provided us with valuable insights into the patterns and behaviors of different threat actors. Additionally, the visualizations reveal a shared, domain-based C&C infrastructure among most Lumma Stealer affiliates. At the same time, we were able to identify less frequently used C&C domains, which we suspect have been reserved for higher tier affiliates or more important campaigns.
Dynamic properties of Lumma Stealer
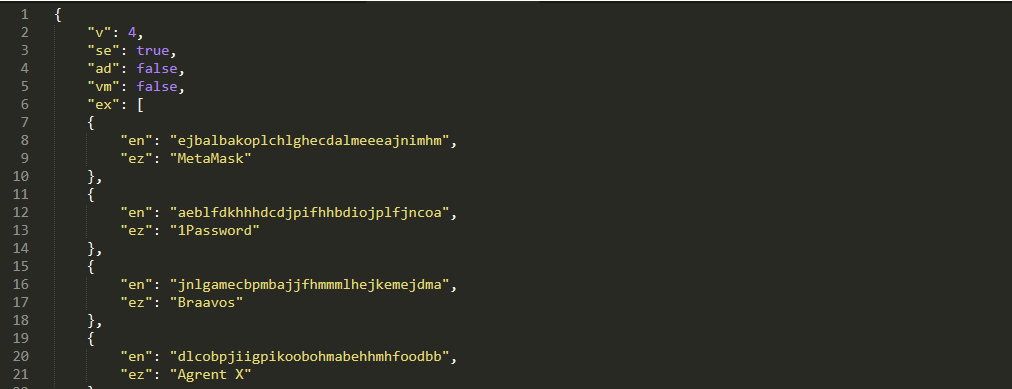
Lumma Stealer retrieves a dynamic configuration from the C&C server, which contains definitions specifying what to scan for exfiltration (see Table 1). The primary focus is on stealing web browser extension data and databases containing passwords, session cookies, web browsing history, and autofill data. Besides web browsers, it also focuses on stealing data from password managers, VPNs, FTP clients, cloud services, remote desktop applications, email clients, cryptocurrency wallets, and note-taking applications.
Table 1. Dynamic config’s JSON fields
| Key | Description |
| v | Dynamic config version. |
| se | Option for taking a screenshot of the victim’s machine for exfiltration. |
| ex | List of Chromium-based browser extensions to target for exfiltration. Each entry consists of: · The extension ID, stored as en. · The extension name, stored as ez. |
| c | Definition of files targeted for exfiltration. The most interesting entries are: · The path for file scanning, stored as p. · The file extension list filter for exfiltration, stored as m. · The maximum folder scanning depth, stored as d. · The maximum file size for exfiltration, stored as fs. |
Even though we haven’t seen significant changes in the default configurations, this feature enhances the malware’s ability to perform targeted exfiltration (see Figure 13). A comprehensive overview of the configuration fields has already been well documented in this research by SpyCloud.
The configuration is in JSON format, and it is downloaded from the C&C server using an HTTPS POST request that includes the LID identifier, optional J parameter, and a specific hardcoded User-Agent string.
The protection of the dynamic configuration has changed a few times recently. Formerly, it was protected in the same way as the static C&C list, by a 32-byte XOR function and base64 encoding. In March 2025 the protection changed to ChaCha20, where the key and nonce were prepended to the encrypted configuration.
The User-Agent string is important to follow, as providing it correctly is essential for receiving the dynamic configuration. In April 2025, Lumma Stealer introduced an additional layer of obfuscation by encrypting JSON values using an 8-byte XOR function (see Figure 14).
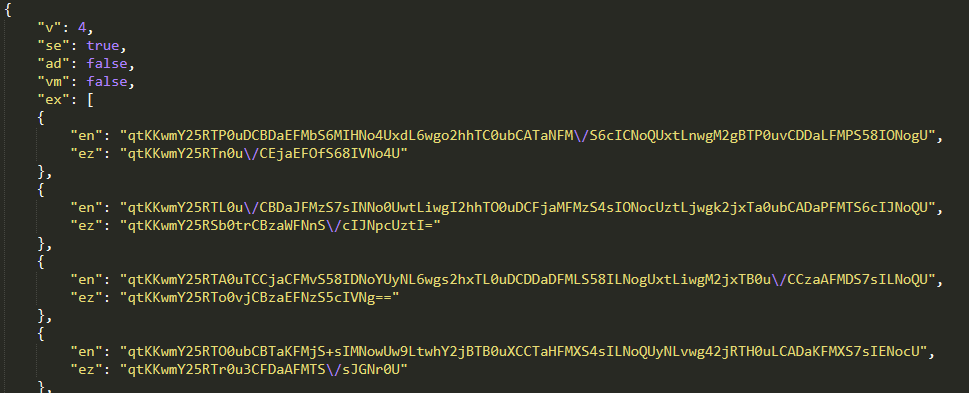
This encrypted variant of the dynamic configuration is delivered when a slightly updated User-Agent string is specified (see Table 2).
Table 2. User-Agent variants
| User-Agent | Description |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36 | Old User-Agent string resulting in a dynamic configuration variant shown in Figure 13. |
| Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36 | New User-Agent string resulting in a dynamic configuration variant with encryption of some values (Figure 14). |
Besides this dynamic configuration approach, Lumma Stealer samples still contain hardcoded instructions for exfiltrating files. These include data from applications such as Outlook or Thunderbird, Steam account information, and Discord account tokens (see this SpyCloud blogpost). This combination of dynamic and hardcoded configurations ensures that Lumma Stealer can effectively collect a wide range of valuable data.
To summarize all the static and dynamic changes mentioned so far, we have created a timeline (Figure 15) highlighting the most significant developments observed in the Lumma Stealer malware over the past year.
C&C communication
Throughout our Lumma Stealer tracking period, all extracted C&C domains consistently led to Cloudflare services, which are utilized to conceal Lumma Stealer’s real C&C infrastructure. Cloudflare services are also employed for C&C servers located via dead-drop resolvers.
First, Lumma Stealer needs to obtain an active C&C server. The mechanism of this choice is illustrated in the flow chart shown in Figure 16.
Handshake
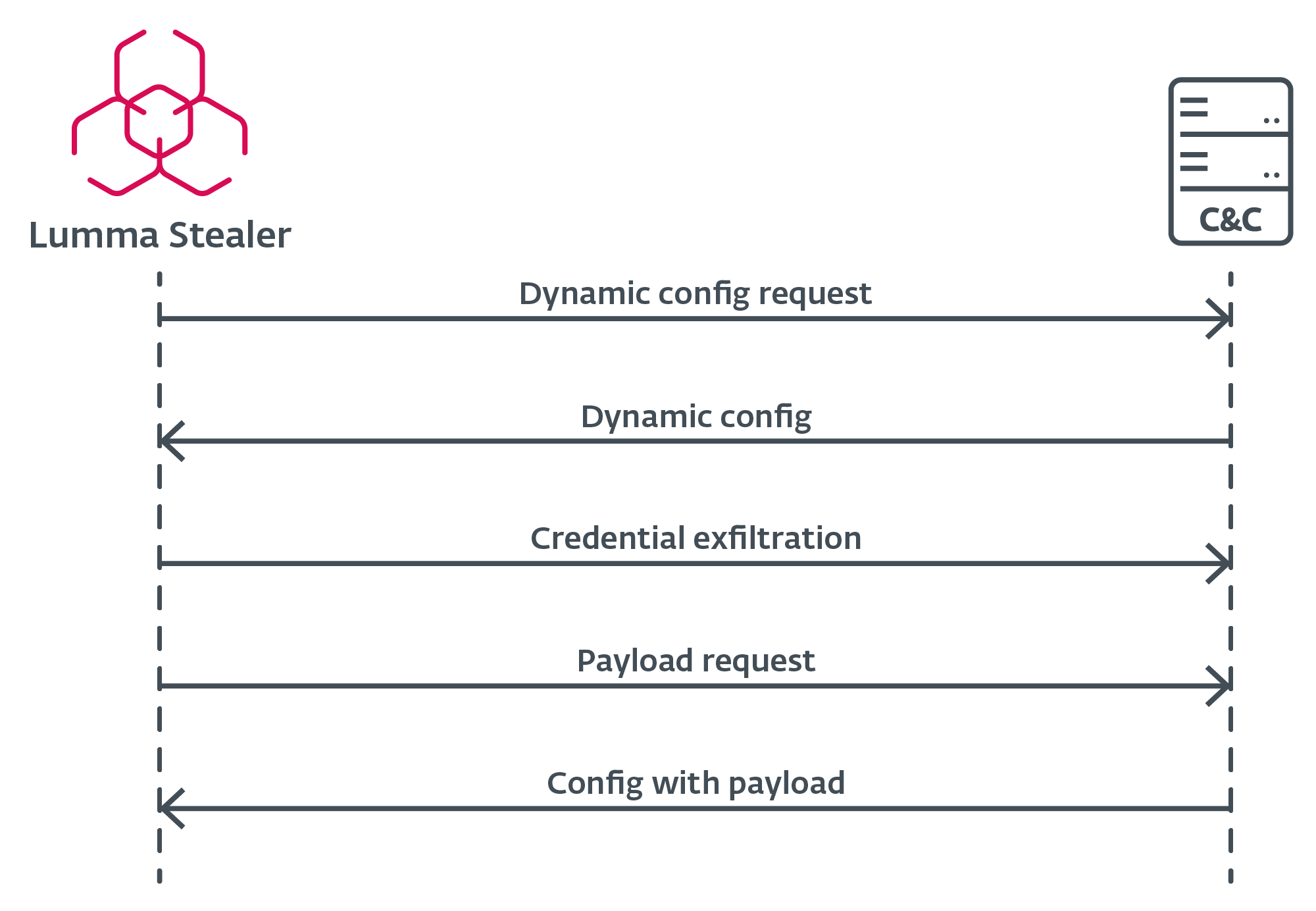
Although the actual handshake request to the C&C server is not present in the latest Lumma Stealer builds, it is worth mentioning because it was a feature of our tracking for a long time. The handshake request was an HTTPS POST request containing act=live and a hardcoded User-Agent. Active servers responded with a cleartext ok message.
Configuration request
When Lumma Stealer identifies an active C&C server, it requests the configuration via an HTTPS POST request (Figure 17), which includes the LID and J parameters as data. If the J parameter is not present in the sample, Lumma Stealer retrieves the default configuration from the C&C server. This configuration specifies what to scan for exfiltration, allowing the malware to adapt to different targets and environments.
Additional payload execution
After Lumma Stealer successfully exfiltrates sensitive data and harvested credentials, it issues one final HTTPS POST request to the C&C server – this time, with an additional victim hardware ID called hwid. This final request retrieves a configuration of an additional payload to be executed on the victim’s machine. The payload or a URL to download from is part of that configuration. Note that such a payload is not always provided.
Anti-analysis obfuscation techniques
Lumma Stealer employs a few, but effective, anti-emulation techniques to make analysis as complicated as possible. These techniques are designed to evade detection and hinder the efforts of security analysts.
Indirect jump obfuscation
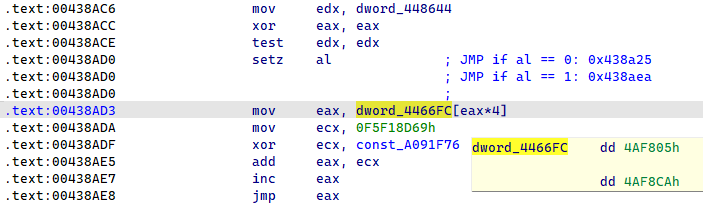
One of the primary obfuscation techniques used by Lumma Stealer is indirect control flow flattening, shown in Figure 18. This method effectively disrupts the code blocks of the functions, making it nearly impossible to keep track of the function logic. By flattening the control flow, the malware obfuscates its operations, complicating the analysis process. For a detailed exploration of this technique and thorough analysis of these obfuscation patterns, along with an outline of the solution, you can refer to this comprehensive article by Mandiant.
Stack strings
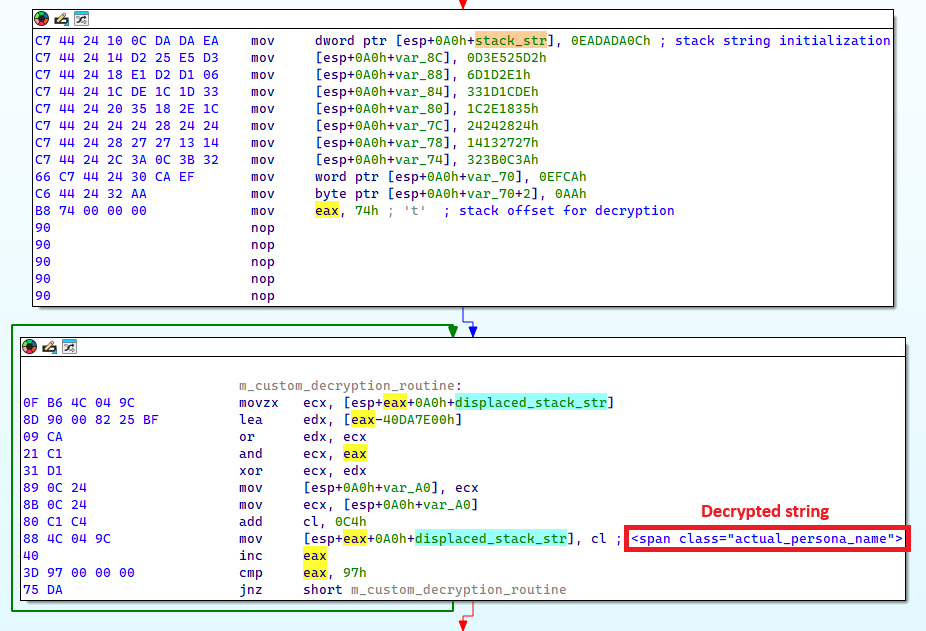
Another technique employed by Lumma Stealer is the use of encrypted stack strings, as illustrated in Figure 19. This method effectively hides binary data and many important strings in the Lumma Stealer sample, making static analysis of the binary difficult. Moreover, each encrypted string has its own unique mathematical function for decryption, adding another layer of complexity to the analysis process.
Import API obfuscation
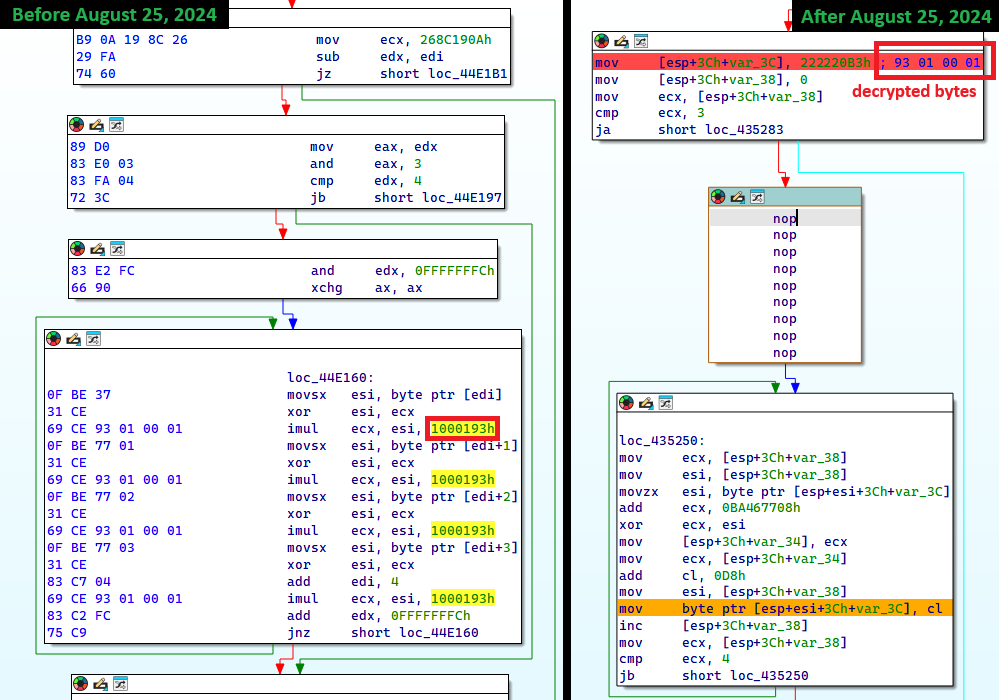
In Lumma Stealer, imports are resolved at runtime. Import names are hashed using the FNV-1a algorithm with each build using a custom offset basis. As shown in Figure 20, since August 25th, 2024, Lumma Stealer also obfuscates the FNV hash algorithm parameters by using stack strings.
Conclusion
This global disruption operation was made possible by our long-term tracking of Lumma Stealer, which we have provided an overview of in this blogpost. We have described the modus operandi of the Lumma Stealer group and its service. Additionally, we have documented the important static identifiers and C&C communication as well as its evolution over the last year. Finally, we summarized the key obfuscation techniques that make the analysis of Lumma Stealer challenging.
The disruption operation, led by Microsoft, aims to seize all known Lumma Stealer C&C domains, rendering Lumma Stealer’s exfiltration infrastructure nonfunctional. ESET will continue to track other infostealers while closely monitoring for Lumma Stealer activity following this disruption operation.
For any inquiries about our research published on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Research offers private APT intelligence reports and data feeds. For any inquiries about this service, visit the ESET Threat Intelligence page.
IoCs
SHA-1
Filename
Detection
Description
6F94CFAABB19491F2B8E
AcroRd32.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-06-27.
C5D3278284666863D758
Notion.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-07-14.
5FA1EDC42ABB42D54D98
explorer.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-08-08.
0D744811CF41606DEB41
aspnet_regiis
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-08-25.
2E3D4C2A7C68DE2DD31A
nslookup.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-09-20.
09734D99A278B3CF59FE
nslookup.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-10-04.
1435D389C72A5855A5D6
BitLockerToGo
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-11-09.
2CCCEA9E1990D6BC7755
external.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2024-12-23.
658550E697D9499DB782
Wemod-Premium-Unlocker-2025
MSIL/GenKryptik.HGWU
Lumma Stealer sample – Build 2025-01-18.
070A001AC12139CC1238
khykuQw.exe
Win32/Kryptik.HYUC
Lumma Stealer sample – Build 2025-02-27.
1FD806B1A0425340704F
Start.exe
Win64/Injector.WR
Lumma Stealer sample – Build 2025-03-24.
F4840C887CAAFF0D5E07
loader.exe
Win64/Kryptik.FAZ
Lumma Stealer sample – Build 2025-04-15.
8F58C4A16717176DFE3C
Set-up.exe
Win32/Spy.Lumma Stealer.B
Lumma Stealer sample – Build 2025-04-23.
Network
| IP | Domain | Hosting provider | First seen | Details |
| 172.67.134[.]100 | cooperatvassquaidmew[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.175[.]165 | crisisrottenyjs[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.96[.]1 | deadtrainingactioniw[.]xyz tamedgeesy[.]sbs nighetwhisper[.]top |
Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.141[.]43 | exuberanttjdkwo[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.96[.]3 | grandcommonyktsju[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 104.21.92[.]96 | qualificationjdwko[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 172.67.209[.]200 | sweetcalcutangkdow[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 104.21.49[.]80 | wordingnatturedowo[.]xyz | Cloudflare, Inc. | 2024‑06‑27 | Lumma Stealer C&C server. |
| 188.114.97[.]0 | bigmouthudiop[.]shop froytnewqowv[.]shop locatedblsoqp[.]shop stagedchheiqwo[.]shop |
Cloudflare, Inc. | 2024‑07‑16 | Lumma Stealer C&C server. |
| 104.21.19[.]156 | callosallsaospz[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.153[.]40 | indexterityszcoxp[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.192[.]52 | lariatedzugspd[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.213[.]85 | liernessfornicsa[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.137[.]78 | outpointsozp[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.221[.]214 | shepherdlyopzc[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.204[.]158 | unseaffarignsk[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 172.67.178[.]194 | upknittsoappz[.]shop | Cloudflare, Inc. | 2024‑07‑18 | Lumma Stealer C&C server. |
| 188.114.97[.]3 | bassizcellskz[.]shop byteplusx[.]digital sparkiob[.]digital longitudde[.]digital |
Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.47[.]141 | celebratioopz[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.158[.]159 | complaintsipzzx[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.204[.]20 | deallerospfosu[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.35[.]48 | languagedscie[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.73[.]43 | mennyudosirso[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 188.114.97[.]9 | quialitsuzoxm[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 172.67.166[.]231 | writerospzm[.]shop | Cloudflare, Inc. | 2024‑08‑07 | Lumma Stealer C&C server. |
| 104.21.16[.]180 | caffegclasiqwp[.]shop | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 172.67.146[.]35 | condedqpwqm[.]shop | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| N/A | evoliutwoqm[.]shop | N/A | 2024‑08‑24 | Lumma Stealer C&C server. |
| 188.114.96[.]0 | millyscroqwp[.]shop stamppreewntnq[.]shop advennture[.]top |
Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 104.21.67[.]155 | traineiwnqo[.]shop | Cloudflare, Inc. | 2024‑08‑24 | Lumma Stealer C&C server. |
| 94.140.14[.]33 | achievenmtynwjq[.]shop carrtychaintnyw[.]shop chickerkuso[.]shop metallygaricwo[.]shop milldymarskwom[.]shop opponnentduei[.]shop puredoffustow[.]shop quotamkdsdqo[.]shop bemuzzeki[.]sbs exemplarou[.]sbs exilepolsiy[.]sbs frizzettei[.]sbs invinjurhey[.]sbs isoplethui[.]sbs laddyirekyi[.]sbs wickedneatr[.]sbs |
Cloudflare, Inc. | 2024‑09‑21 | Lumma Stealer C&C server. |
| 188.114.97[.]4 | usseorganizedw[.]shop bellflamre[.]click tripfflux[.]world |
Cloudflare, Inc. | 2024‑09‑24 | Lumma Stealer C&C server. |
| 104.21.44[.]84 | beerishint[.]sbs | Cloudflare, Inc. | 2024‑10‑06 | Lumma Stealer C&C server. |
| 104.21.64[.]84 | 1212tank.activitydmy[.]icu | Cloudflare, Inc. | 2024‑11‑12 | Lumma Stealer C&C server. |
| 104.21.93[.]246 | brownieyuz[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.189[.]210 | ducksringjk[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.146[.]64 | explainvees[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 104.21.90[.]226 | relalingj[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 104.21.14[.]17 | repostebhu[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 172.67.192[.]43 | rottieud[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 188.114.97[.]1 | thinkyyokej[.]sbs | Cloudflare, Inc. | 2024‑11‑08 | Lumma Stealer C&C server. |
| 188.114.97[.]7 | bashfulacid[.]lat tentabatte[.]lat |
Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.21.86[.]54 | curverpluch[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.21.66[.]86 | lev‑tolstoi[.]com | Cloudflare, Inc. | 2024‑12‑17 | Lumma Stealer C&C server. |
| 172.64.80[.]1 | manyrestro[.]lat toppyneedus[.]biz |
Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 188.114.97[.]2 | shapestickyr[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 172.67.192[.]247 | slipperyloo[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 104.105.90[.]131 | steamcommunity[.]com steamcommunity[.]com |
Akamai Technologies, Inc. | 2024‑06‑27 | Steam profile dead‑drop resolvers. |
| 172.67.146[.]68 | talkynicer[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| 172.67.184[.]241 | wordyfindy[.]lat | Cloudflare, Inc. | 2024‑12‑23 | Lumma Stealer C&C server. |
| N/A | beevasyeip[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | broadecatez[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | encirelk[.]cyou | N/A | 2025‑01‑28 | Lumma Stealer C&C server. |
| N/A | granystearr[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | quarrelepek[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | rockemineu[.]bond | N/A | 2025‑01‑28 | Lumma Stealer C&C server. |
| 104.21.19[.]91 | suggestyuoz[.]biz | Cloudflare, Inc. | 2025‑01‑22 | Lumma Stealer C&C server. |
| N/A | tranuqlekper[.]bond | N/A | 2025‑01‑22 | Lumma Stealer C&C server. |
| 104.21.69[.]194 | codxefusion[.]top | Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.80[.]1 | earthsymphzony[.]today climatologfy[.]top |
Cloudflare, Inc. | 2025‑02‑26 | Lumma Stealer C&C server. |
| 104.21.88[.]16 | experimentalideas[.]today | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 172.67.146[.]181 | gadgethgfub[.]icu | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 104.21.48[.]238 | hardrwarehaven[.]run | Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.16[.]1 | hardswarehub[.]today pixtreev[.]run |
Cloudflare, Inc. | 2025‑02‑28 | Lumma Stealer C&C server. |
| 104.21.39[.]95 | quietswtreams[.]life | Cloudflare, Inc. | 2025‑02‑26 | Lumma Stealer C&C server. |
| 172.67.222[.]46 | socialsscesforum[.]icu | Cloudflare, Inc. | 2025‑03‑03 | Lumma Stealer C&C server. |
| 172.67.191[.]187 | techmindzs[.]live | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 172.67.214[.]226 | techspherxe[.]top | Cloudflare, Inc. | 2025‑03‑01 | Lumma Stealer C&C server. |
| 104.21.26[.]124 | appgridn[.]live | Cloudflare, Inc. | 2025‑03‑24 | Lumma Stealer C&C server. |
| 172.67.178[.]7 | lunoxorn[.]top | Cloudflare, Inc. | 2025‑03‑31 | Lumma Stealer C&C server. |
| 104.21.47[.]117 | skynetxc[.]live | Cloudflare, Inc. | 2025‑03‑24 | Lumma Stealer C&C server. |
| 104.21.72[.]121 | targett[.]top | Cloudflare, Inc. | 2025‑03‑20 | Lumma Stealer C&C server. |
| 188.114.96[.]2 | travewlio[.]shop | Cloudflare, Inc. | 2025‑03‑20 | Lumma Stealer C&C server. |
| 104.21.42[.]7 | changeaie[.]top | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 104.21.85[.]126 | clarmodq[.]top | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.161[.]40 | liftally[.]top | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.176[.]107 | piratetwrath[.]run | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 172.67.215[.]114 | quilltayle[.]live | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 172.67.143[.]12 | salaccgfa[.]top | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 104.21.5[.]146 | starofliught[.]top | Cloudflare, Inc. | 2025‑04‑17 | Lumma Stealer C&C server. |
| 104.21.32[.]1 | zestmodp[.]top | Cloudflare, Inc. | 2025‑04‑08 | Lumma Stealer C&C server. |
| 172.67.147[.]123 | equatorf[.]run | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 104.21.112[.]1 | hemispherexz[.]top | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 104.21.20[.]106 | latitudert[.]live | Cloudflare, Inc. | 2025‑04‑21 | Lumma Stealer C&C server. |
| 172.67.216[.]12 | sectorecoo[.]live | Cloudflare, Inc. | 2025‑04‑19 | Lumma Stealer C&C server. |
MITRE ATT&CK techniques
This table was built using version 17 of the MITRE ATT&CK framework.
| Tactic | ID | Name | Description |
| Resource Development | T1587.001 | Develop Capabilities: Malware | Lumma Stealer operators actively developed their malware as a product for their service. |
| T1583.001 | Acquire Infrastructure: Domains | Lumma Stealer operators registered domains for their exfiltration infrastructure. | |
| T1583.006 | Acquire Infrastructure: Web Services | Lumma Stealer operators used Cloudflare services to hide their infrastructure. Lumma Stealer also hid its C&C URLs in public services like dummy Steam profiles or empty Telegram channels. | |
| Execution | T1059.003 | Command-Line Interface: Windows Command Shell | Lumma Stealer executes cmd.exe to delete temporary files. |
| T1106 | Native API | Lumma Stealer executes a variety of Windows APIs, including VirtualAlloc, LoadLibraryA, and GetProcAddress. | |
| T1204.001 | User Execution: Malicious Link | Lumma Stealer operators offer a simple LNK packing feature for their malware builds. | |
| T1047 | Windows Management Instrumentation | Lumma Stealer uses WMI queries to gather system information. | |
| Defense Evasion | T1622 | Debugger Evasion | Lumma Stealer checks for debugger presence. |
| T1140 | Deobfuscate/Decode Files or Information | Lumma Stealer uses ChaCha20 for C&C list and dynamic config encryption. | |
| T1027.007 | Obfuscated Files or Information: Dynamic API Resolution | Lumma Stealer resolves API names at runtime using the FNV-1a hash algorithm. | |
| T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File | Lumma Stealer encrypts strings and important binary data using stack strings or ChaCha20. | |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers | Lumma Stealer gathers credentials from multiple browsers. |
| T1539 | Steal Web Session Cookie | Lumma Stealer gathers cookies from multiple browsers. | |
| Discovery | T1217 | Browser Bookmark Discovery | Lumma Stealer checks and collects various information about installed browsers on victims’ machines. |
| T1012 | Query Registry | Lumma Stealer queries registry keys to list installed software on victims’ machines. | |
| T1057 | Process Discovery | Lumma Stealer sends the process list to its C&C server. | |
| T1518 | Software Discovery | Lumma Stealer sends a list of installed software to its C&C server. | |
| T1082 | System Information Discovery | Lumma Stealer sends system information to its C&C server. | |
| T1124 | System Time Discovery | Lumma Stealer sends the current system time and time zone to its C&C server. | |
| Collection | T1560 | Archive Collected Data | Lumma Stealer compresses gathered data before exfiltration to its C&C server. |
| T1119 | Automated Collection | Lumma Stealer’s exfiltration capabilities are fully automated and based on a configuration file. | |
| T1113 | Screen Capture | Lumma Stealer takes screenshots of victims’ machines based on dynamic configuration. | |
| T1005 | Data from Local System | Lumma Stealer collects local system data from victims’ machines. | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols | Lumma Stealer uses HTTPS communication with its C&C servers. |
| T1132.001 | Data Encoding: Standard Encoding | Lumma Stealer used base64 encoding for obtaining its configuration from the C&C server. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | Lumma Stealer uses additional ChaCha20 encryption under the HTTPS network protocol. | |
| T1008 | Fallback Channels | Lumma Stealer employs backup dead-drop resolvers in Steam profiles and Telegram channels. | |
| T1102.001 | Web Service: Dead Drop Resolver | Lumma Stealer employs backup dead-drop resolvers in Steam profiles and Telegram channels. | |
| Exfiltration | T1020 | Automated Exfiltration | Lumma Stealer exfiltrates stolen credentials and data over the C&C channel. |
| T1041 | Exfiltration Over C2 Channel | Lumma Stealer exfiltrates stolen credentials and data over the C&C channel. |

